Logs Monitoring in Microservices using ELK - Architecture
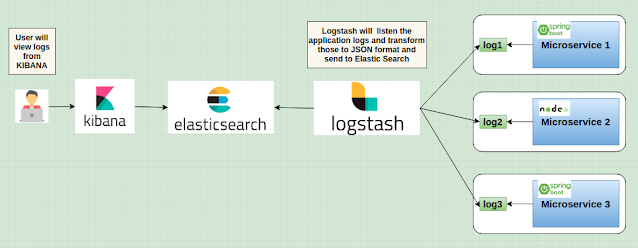
The ELK Stack is an amassment of three open-source products — Elasticsearch, Logstash, and Kibana. ELK stack provides centralized logging in order to identify quandaries with servers or applications. It sanctions us to search all the logs in a single place. It withal avails to find issues in multiple servers by connecting logs during a concrete time frame. The ELK stack provides a simple yet robust log analysis solution for our developers and DevOps engineers to gain valuable insights on failure diagnosis, application performance, and infrastructure monitoring. Modern log management and analysis solutions include the following capabilities: Aggregation – the facility to accumulate and ship logs from multiple data sources. Processing – the faculty to transform log messages into consequential data for more facile analysis. Storage – the faculty to store data for elongated time periods to sanction for monitoring, trend analysis, and security use cases. Analysis – the faculty to dissec




